Welcome to RailsGoat
Tutorial Guide
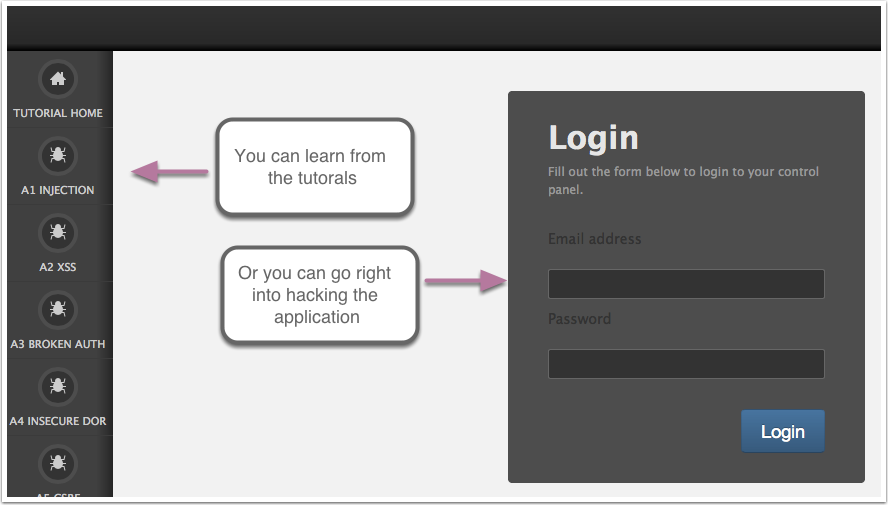
Step 1 - Choose your path
Get Started
Choose your path! Go directly into reading each tutorial or begin attacking the application to practice identifying weaknesses.
You can then cross reference your findings with the findings listed under the tutorials section.
Step 2 - Using the application
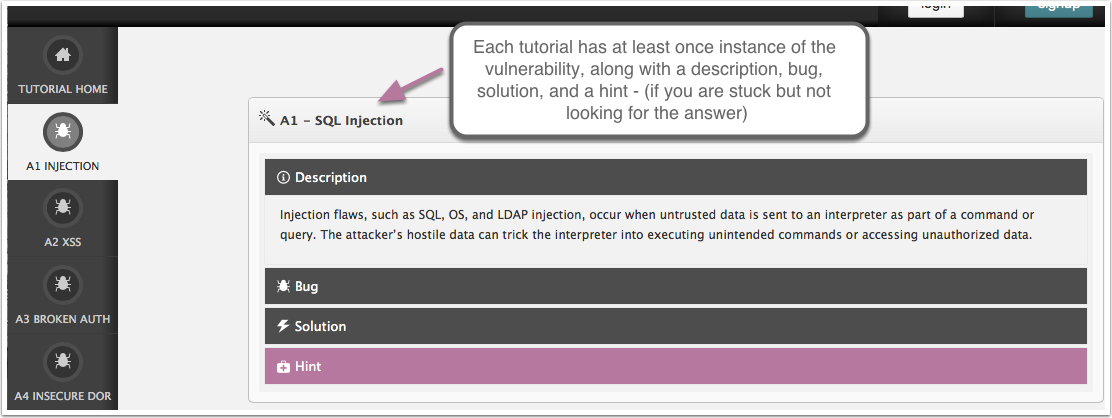
Using the application
Each tutorial offers 4 parts:
These titles are fairly self-explanatory but BEWARE, the solution section gives away how to solve or attack that particular vulnerability instance!
Step 3 - Attack
HACK!